This depends on what BIOS the machine has. Common BIOS’s include AMI, Award, IBM and Phoenix. Numerous other BIOS’s do exist, but these are the most common.
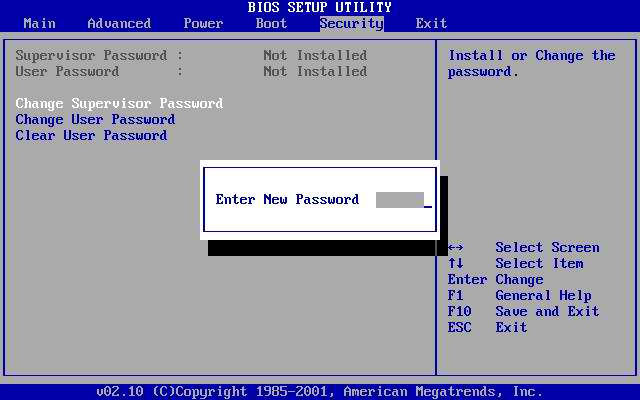
Some BIOS’s allow you to require a password be entered before the system will boot. Some BIOS’s allow you to require a password to be entered before the BIOS setup may be accessed.
Every BIOS must store this password information somewhere. If you are able to access the machine after it has been booted successfully, you may be able to view the password. You must know the memory address where the password is stored, and the format in which the password is stored. Or, you must have a program that knows these things.
The most common BIOS password attack programs are for Ami BIOS. Some password attack programs will return the AMI BIOS password in plain text, some will return it in ASCII codes, some will return it in scan codes. This appears to be dependent not just on the password attacker, but also on the version of Ami BIOS.
To obtain Ami BIOS password attackers, ftp to oak.oakland.edu/simtel/msdos/sysutil/.
If you cannot access the machine after if has been powered up, it is still possible to get past the password. The password is stored in CMOS memory that is maintained while the PC is powered off by a small battery, which is attached to the motherboard. If you remove this battery, all CMOS information will be lost. You will need to re-enter the correct CMOS setup information to use the machine. The machines owner or user will most likely be alarmed when it is discovered that the BIOS password has been deleted.
On some motherboards, the battery is soldered to the motherboard, making it difficult to remove. If this is the case, you have another alternative. Somewhere on the motherboard you should find a jumper that will clear the BIOS password. If you have the motherboard documentation, you will know where that jumper is. If not, the jumper may be labeled on the motherboard. If you are not fortunate enough for either of these to be the case, you may be able to guess which jumper is the correct jumper. This jumper is usually standing alone near the battery.